Getting Started
When it comes to securing your Azure Logic App, there are multiple steps that can be taken to achieve this. One of these steps have been used in previous blogged solutions, which is encrypting the Input and Output of the actions used within your Logic App. This is already a good practise when it comes to masking sensitive data and not being able to recall the data from the Logic Apps Run History. Another solution would be to add OAuth to your Logic App when it contains an HTTP Trigger, but that is something for another blog. This blog will focus on the restricting who can call upon your Logic App when using an HTTP Trigger, but from a networking point of view and how to embed this in your Infrastructure as Code.
Lets get started!
Access Control
Within the Workflow settings tab of your Azure Logic App, which you can find underneath the Settings category in the blade of your Logic App, you will see the Access control configuration option. Here you will find 2 options: Trigger access and IP ranges for contents. The IP ranges for contents restricts calls made to your Logic App and only allow specific IPs to get Inputs and Outputs from the Run History.
The Trigger access option is the interesting one to look at, especially since this restricts who can call the Logic app in the first place.
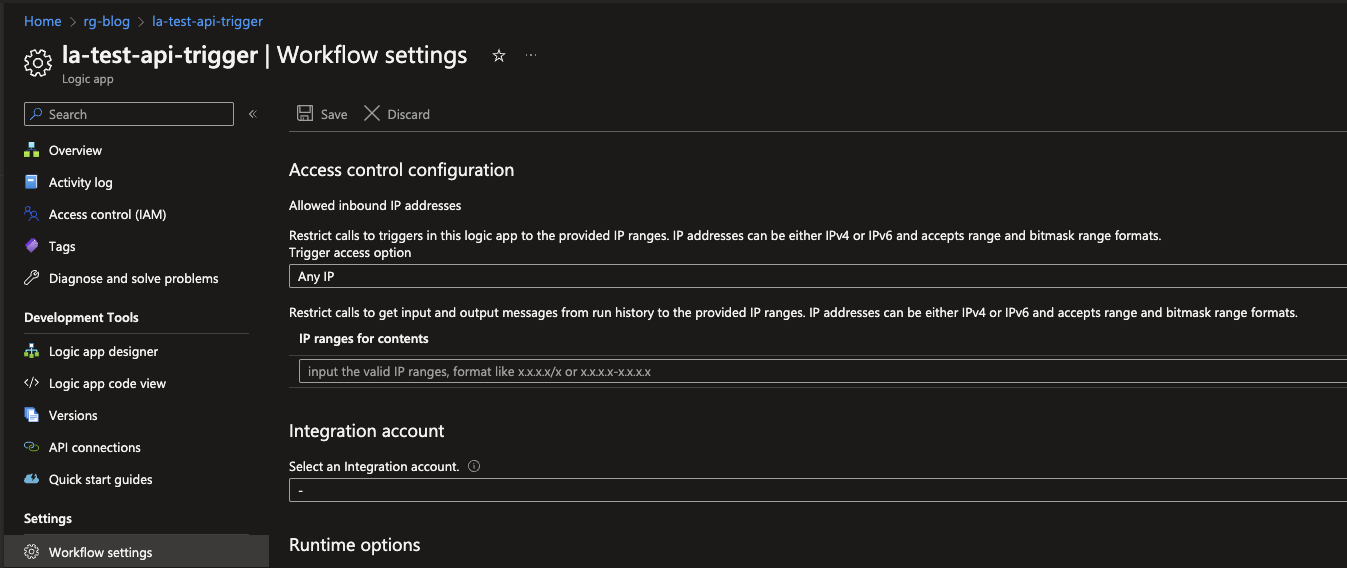
The Trigger access option comes currently in 3 flavours:
- Any IP, allowing everyone who knows the Logic Apps Endpoint to call it and trigger it in the process.
- Only other Logic Apps, allowing only other Logic Apps to call the Logic App.
- Specific IP ranges, Only allowing specified IP ranges to call the Logic App.
As you might guess the latter, would be recommended option to use.
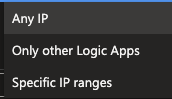
If we dive a bit deeper in the Specific IP ranges, you will be able to specify a range in the format of 66.231.80.0-66.231.95.255 or a specific static IP address such as 54.254.118.123/32. This follows the x.x.x.x-x.x.x.x and x.x.x.x/x pattern accordingly and allows your Logic App to only be called via these IP addresses.
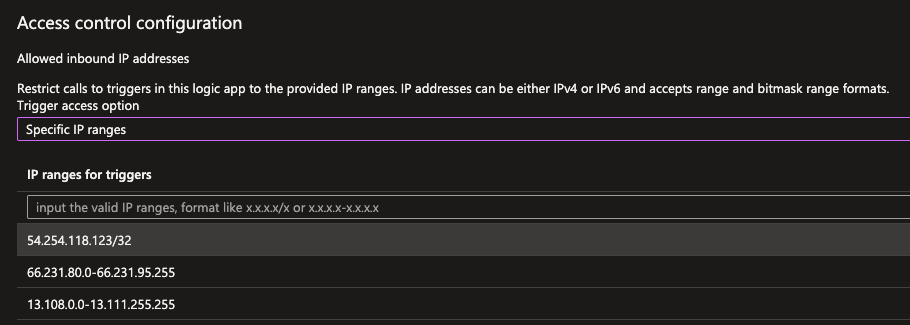
If your IP address is not registered and you will make a call to the Logic App endpoint you will receive an Unauthorized error. When this happens, the Logic App will fail immediately and no further actions will be executed. The Specific IP ranges option is a nice safeguard to have in place and makes a great default in Logic App deployments via Infrastructure as Code (IaC).
When it comes to IaC for the Access control configuration it can be quit tedious, so lets see how to do it!
Infrastructure as Code
When it comes to deploying services I often tend to check the configuration in the Azure Portal via the Export Template option. Unfortunatly the Workflow settings of the Logic App are not being exported from the Portal or shown what so ever.
Luckily https://resources.azure.com/ was introduced, which allows you to make API calls to the Resource Manager and check how everything looks like as it actually is configured, making it also show the Access control settings. While this might be shown in JSON, it is not much different for a Bicep which makes it easy to adjust and add to the IaC.
Now with the right properties exposed you should think this would be a walk in the park, and it will be after this, but the configuration never showed any form of the Any IP, Only other Logic Apps or Specific IP ranges option. With some trail and error, I figured out the mapping for these options and they are as followed:
accessControl: {} = Any IP
accessControl:
triggers: {
allowedCallerIpAddresses: []
}
actions: {
allowedCallerIpAddresses: []
}
}= Only other Logic Apps
accessControl:
triggers: {
allowedCallerIpAddresses: [
{
addressRange: 'IP'
}
]
}
actions: {
allowedCallerIpAddresses: [
{
addressRange: 'IP'
}
]
}= Specific IP ranges
You can parameterize the above code accordingly, creating an array with multiple { addressRange: 'IP' } to easily add your list of IP addresses. In case no IP addresses are required but we want to keep it restricted to Only other Logic Apps you just let the array be [] and your good to go!
What's Next?
Since I'm on the topic of Logic App security, lets look how to apply Oauth to our Logic App Endpoints and make them even more secure! stay tuned for next weeks blog!

